Profitably Repurpose PLR Digital Content into Unique Market Offerings
Repurposing Private Label Rights PLR digital content can be a highly effective strategy for creating unique market offerings while saving time and effort. PLR content provides a solid foundation, offering ready-made materials like articles, eBooks, and videos that you can legally modify and brand as your own. However, to turn this generic content into a profitable asset, it is crucial to approach repurposing with creativity, ensuring that the final product is distinct and valuable to your target audience. Not all PLR content is created equal, so it is essential to select materials that align with your niche or the specific problem your audience faces. Once you have found suitable content, the key is to inject originality into it. Start by rewriting or expanding the content. This can include rewording sections, adding new sections, or rearranging the information to create a fresh perspective. For example, an eBook that covers a general topic can be rewritten to focus more deeply on a subtopic that is particularly relevant to your audience.
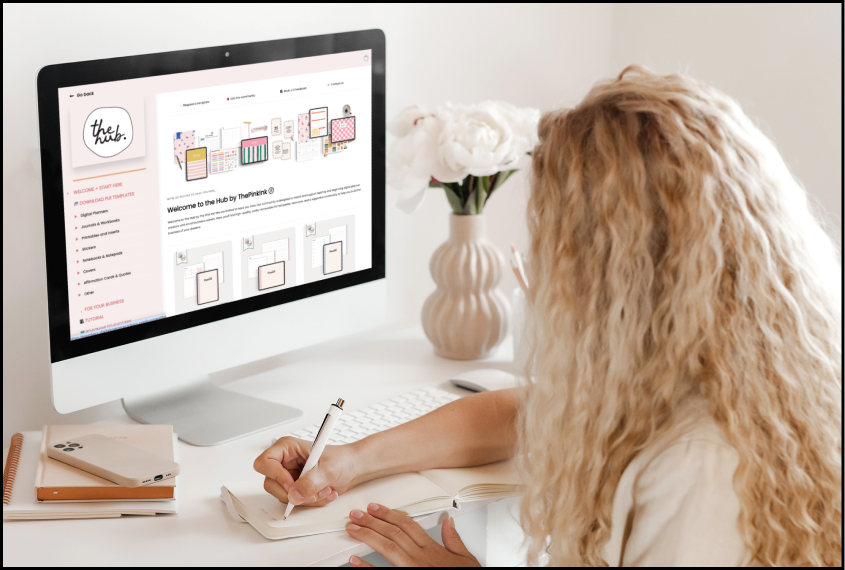
Another approach to repurposing PLR content is to combine multiple pieces into a new offering and why not try these out plrdigitalproducts.net. If you have several PLR articles or resources on a related subject, you can consolidate them into a comprehensive guide, course, or workbook. This method allows you to add your expertise by providing commentary, personal insights, or case studies that enrich the original content. By combining multiple PLR pieces, you create a more valuable and authoritative resource that your audience is willing to pay for. To further differentiate your offering, consider adding multimedia elements. If the original PLR content is text-based, turning it into a video, podcast, or infographics can significantly enhance its appeal. A video course, for instance, can present the same information as the original text, but in a more engaging, dynamic format that suits visual learners. You can also create supplementary resources like worksheets, quizzes, or cheat sheets that reinforce the concepts in the PLR content, offering a more interactive and personalized experience.
One effective method of repurposing is to break down large PLR products into smaller, consumable pieces. For example, if you have a long PLR eBook, you can turn it into a series of blog posts, emails, or mini-guides. This technique not only helps in presenting the content in bite-sized pieces but also keeps your audience engaged over time, ensuring they return for more information. Additionally, repurposing content in smaller formats makes it easier to distribute across multiple platforms, further expanding your reach. Personalization is also an essential aspect of repurposing PLR content. Adding your own voice, style, and examples will make the material feel more authentic. You can also update outdated information, refine language, or add relevant statistics to make it more relevant and current. Personalizing the content creates a stronger connection with your audience and increases the likelihood of conversion. Whether you choose to sell it as a standalone product, bundle it with other offerings, or use it as a lead magnet, the way you present the content matters.
...Discover Success Through Abacus Marketplace’s Secure And Efficient Trading
In today’s fast-paced digital economy, online marketplaces have become a significant part of the trading landscape. These platforms allow individuals and businesses to connect, buy, and sell goods or services from anywhere in the world. A crucial aspect that sets successful online trading platforms apart is their commitment to providing a secure and efficient environment for users. Ensuring that both buyers and sellers can confidently engage in transactions without fear of fraud or mishap is paramount in fostering trust and long-term relationships. One of the core features of a secure online marketplace is the use of robust encryption technologies. These measures protect sensitive user information, such as personal data and payment details, from being intercepted by malicious actors. Encryption ensures that transactions are carried out safely and that users can maintain their privacy. With the increasing threats posed by cyber-attacks and data breaches, implementing cutting-edge security protocols has become non-negotiable for any trading platform that values its users’ trust.

Efficient trading is equally important in today’s competitive market. An efficient marketplace ensures that transactions are processed swiftly and without unnecessary delays. This includes fast payment processing, real-time updates on product availability, and reliable delivery systems. An optimized trading system can handle large volumes of transactions at once, without compromising on performance. Such efficiency not only enhances the user experience but also drives business success by reducing operational costs and increasing customer satisfaction. The platform’s interface plays a vital role in facilitating efficient trading. A well-designed, user-friendly interface allows users to navigate through listings, communicate with sellers, and finalize transactions without confusion or hassle. A clutter-free, intuitive layout helps users find what they are looking for quickly and effectively. By providing advanced search filters, clear product descriptions, and easy checkout options, marketplaces can greatly enhance the overall user experience, making trading as seamless as possible. The key to discovering success through any online Abacus link trading platform lies in the combination of security, efficiency, user-friendly design, trust, and reliable dispute resolution.
In addition to security and efficiency, trust is a cornerstone of success in online trading. A transparent marketplace fosters trust by providing users with clear and accurate information about products, services, and sellers. This includes verified reviews, detailed product specifications, and reliable seller ratings. Transparency not only helps buyers make informed decisions but also encourages sellers to maintain high standards of service, knowing that their reputation is on the line. To further promote trust and success, marketplaces often integrate dispute resolution systems. These systems are designed to handle conflicts between buyers and sellers in a fair and impartial manner. Whether it is an issue with a product’s quality or a delay in delivery, a reliable dispute resolution process helps resolve matters swiftly, ensuring that both parties are satisfied. This added layer of protection ensures that users can trade with peace of mind, knowing that their concerns will be addressed promptly and fairly. As the online trading landscape continues to evolve, maintaining these principles will remain essential for ensuring success and fostering long-term prosperity.
...Why Twitter Reply Automation is Key to Business Growth?
In the rapidly evolving landscape of social media, businesses are increasingly recognizing the power of Twitter as a vital platform for engagement, branding, and customer service. As Twitter’s user base continues to grow, the volume of interactions tweets, retweets, mentions, and replies can become overwhelming for organizations striving to maintain a consistent and effective online presence. This is where Twitter reply automation emerges as a crucial tool for business growth. By automating replies, businesses can enhance their responsiveness, save valuable time, and improve overall customer satisfaction. One of the primary advantages of Twitter reply automation is its ability to ensure timely interactions with customers. In today’s fast-paced digital world, consumers expect immediate responses to their inquiries. Whether it is a question about a product, a complaint, or a request for information, automated replies can provide instant acknowledgment and assistance, significantly reducing response times. This immediacy can foster a positive customer experience, making customers feel valued and heard.
Additionally, quick responses can prevent potential issues from escalating, as timely communication often diffuses tensions and demonstrates a company’s commitment to customer care. Moreover, Twitter reply automation can help businesses maintain a consistent brand voice across all interactions. By employing pre-defined replies that reflect the company’s values and messaging, brands can ensure that all customer interactions are coherent and on-brand, regardless of the volume of inquiries. This consistency helps to build brand identity and trust, which are essential components for long-term customer loyalty. Automation also allows businesses to engage in conversations that might otherwise go unanswered due to time constraints or resource limitations. This increased engagement can lead to higher visibility on the platform, as more interactions can translate into more retweets, likes, and shares, further amplifying the brand’s reach. Additionally, automated X AI Comments can be tailored to fit specific scenarios or frequently asked questions, allowing businesses to provide relevant and helpful information without manual intervention.
This targeted approach not only enhances efficiency but also ensures that customers receive the information they need in a timely manner. Furthermore, the use of automation tools enables businesses to analyze engagement data effectively. By tracking metrics such as response times, engagement rates, and customer feedback, organizations can refine their automated responses and strategies over time. This data-driven approach allows businesses to adapt to changing customer preferences and improve their overall social media strategy, ultimately driving growth. In conclusion, Twitter reply automation is not merely a convenience; it is a strategic necessity for businesses aiming to thrive in a competitive digital landscape. By leveraging automation, companies can enhance their responsiveness, maintain brand consistency, and increase engagement, all of which are essential components for fostering customer loyalty and driving growth. As Twitter continues to be a significant platform for business interaction, adopting automation tools will empower organizations to navigate the complexities of customer engagement more effectively, ensuring they remain relevant and competitive in their industries.
...The Role of Reverse Email Lookup in Professional Networking and Recruitment
In a digital landscape increasingly fraught with cyber threats and deceptive practices, reverse email lookup services have emerged as essential tools for enhancing online security and personal safety. These services allow users to input an email address and retrieve information about the sender, including their name, location, and often additional contact details. As email continues to be a primary mode of communication for both personal and professional interactions, the ability to verify the identity of an email sender has become crucial. Reverse email lookup serves as a safeguard against various forms of online fraud and deception. Phishing frauds, where malicious actors attempt to steal sensitive information by posing as legitimate entities, are a significant concern for individuals and businesses alike. By using reverse email lookup services, users can verify the authenticity of the email sender before responding or clicking on any links, thereby reducing the risk of falling victim to these schemes.

For professionals, reverse email lookup can be particularly beneficial in the context of networking and recruitment. When receiving unsolicited emails or reaching out to potential candidates, verifying the sender’s identity helps ensure that communications are legitimate and relevant. This can enhance the efficiency of networking efforts and prevent wasted time and resources on fraudulent or irrelevant contacts. The process of reverse email lookup typically involves searching through databases those aggregate public records, social media profiles, and other online information to provide details about the email address in question. While these services can offer valuable insights, users should be aware of the limitations and potential privacy concerns associated with them. The accuracy of the information retrieved can vary, and there are legal considerations regarding the use of such data, depending on the jurisdiction.
While reverse email lookup services can offer significant benefits, they also come with inherent risks. Privacy concerns are paramount, as the availability of personal information can be misused if not handled responsibly. It is important for users to choose reputable services that prioritize data security and when was a domain name registered. Additionally, while reverse email lookup can help in identifying fraudulent emails, it is not foolproof. Users should still exercise caution and use other security measures, such as strong passwords and multi-factor authentication, to protect their online accounts. In summary, reverse email lookup services play a vital role in safeguarding against email fraud and enhancing online security. They offer a means to verify the identity of email senders, thereby reducing the risk of falling victim to frauds and ensuring more secure communications. However, users must navigate the potential privacy issues and legal implications carefully, making informed decisions about how and when to utilize these services.
...Master’s in Data Science – Developing Proficiency in Programming Languages
Master’s in Data Science programs equip students with a diverse skill set, emphasizing proficiency in programming languages crucial for data analysis, machine learning, and statistical modeling. Aspiring data scientists often embark on their educational journey with foundational knowledge in programming, which is further honed through specialized coursework and practical applications. Python stands out as the cornerstone programming language in data science education. Renowned for its simplicity and versatility, Python is favored for its extensive libraries, essential for data manipulation, analysis, and visualization. Master’s programs typically begin with Python fundamentals, covering data types, control flow, functions, and object-oriented programming. Advanced topics delve into web scraping, API integration, and parallel computing, preparing students to handle large datasets efficiently. R complements Python, particularly in statistical analysis and data visualization. Master’s programs integrate R to explore statistical modeling techniques, hypothesis testing, and data mining. Students learn to leverage R’s packages like ggplot2 for graphical representations for data manipulation.

Proficiency in R equips graduates with robust statistical skills essential for exploring complex datasets and deriving meaningful insights. SQL proficiency is crucial for data retrieval and management. Master’s programs include SQL training to empower students in querying relational databases, designing schemas, and optimizing database performance. Understanding SQL ensures data scientists can access and manipulate structured data efficiently, crucial for real-time analytics and business intelligence applications. Java and Scala are introduced for their roles in big data processing frameworks like Apache Hadoop and Spark. These languages enable distributed computing, handling massive datasets across clusters. Master’s programs familiarize students with Java for its scalability and robustness, while Scala’s concise syntax facilitates seamless integration with Spark, enhancing data processing capabilities for large-scale analytics projects. JavaScript proficiency is relevant for web-based data visualization and interactive dashboards. Master’s programs incorporate JavaScript frameworks like D3.js and Plotly, empowering students to create dynamic visualizations that communicate insights effectively.
is a masters in data science worth it JavaScript skills are essential for front-end development in data-driven applications, enhancing user experience through responsive design and interactive data displays. MATLAB remains prevalent in academic research and engineering applications, particularly in signal processing and numerical computing. Master’s programs may include MATLAB for its mathematical modeling capabilities, teaching students to implement algorithms and simulate systems in fields such as image processing and computational biology. C/C++ proficiency is advantageous for performance-critical applications like algorithm optimization and system-level programming. Master’s programs cover these languages to equip students with low-level programming skills essential for developing efficient algorithms and integrating with hardware systems in industries such as finance and cybersecurity. Master’s in Data Science programs prioritize hands-on projects and real-world applications to reinforce programming proficiency. Capstone projects often require students to apply programming skills to solve industry-specific challenges, fostering collaboration with stakeholders and demonstrating the ability to deliver actionable insights from data. By combining theoretical knowledge with practical experience, graduates emerge prepared to drive innovation and make data-driven decisions across diverse industries.
...Automated Efficiency – DevOps Services for Optimized Operations
In the ever-evolving landscape of software development and IT operations, the demand for automated efficiency has become paramount. DevOps, an amalgamation of development and operations, has emerged as a solution to bridge the gap between these traditionally siloed functions. DevOps services offer a systematic approach to streamline workflows, optimize operations, and enhance collaboration among teams, thereby fostering a culture of continuous integration and delivery CI/CD. At its core, DevOps emphasizes automation, enabling organizations to achieve higher levels of efficiency, reliability, and scalability in their software delivery processes. One of the key principles of DevOps is automation, which aims to eliminate manual intervention wherever possible. By automating repetitive tasks such as code deployment, testing, and infrastructure provisioning, teams can significantly reduce the risk of human error and accelerate the pace of delivery. Continuous Integration CI and Continuous Delivery CD pipelines serve as the backbone of automation in DevOps, facilitating the seamless integration of code changes into the main repository and the automated deployment of applications to various environments.

This automated approach not only enhances efficiency but also ensures consistency across development, testing, and production environments, leading to improved quality and faster time-to-market. Moreover, DevOps services leverage infrastructure as code IaC to automate the provisioning and management of infrastructure resources. By defining infrastructure configurations through code, teams can easily replicate environments, deploy applications consistently, and scale resources on-demand. Tools such as Terraform, Ansible, and Chef enable infrastructure automation by providing declarative or imperative approaches to define and manage infrastructure components. This shift towards codifying infrastructure not only enhances operational efficiency but also promotes infrastructure consistency, reliability, and version control, thereby reducing deployment errors and minimizing downtime. Furthermore, DevOps services promote collaboration and communication across development, operations, and other stakeholders within the organization. By breaking down organizational silos and fostering a culture of shared responsibility, DevOps encourages teams to collaborate closely throughout the software development lifecycle SDLC.
Cross-functional teams collaborate on designing, implementing, testing, deploying, and monitoring applications, enabling faster feedback loops and iterative improvements. Collaboration tools such as Slack, Microsoft Teams, and Jira facilitate real-time communication, collaboration, and knowledge sharing among team members, regardless of their geographical locations and find more info in this website https://quema.co/contact. In addition, DevOps services emphasize monitoring and observability to ensure the reliability and performance of applications in production environments. By implementing monitoring tools and practices, such as logging, metrics, and tracing, teams can gain insights into the behavior of applications and infrastructure components, identify performance bottlenecks, and proactively detect and resolve issues before they impact end-users. Continuous monitoring enables teams to maintain the health and availability of applications, optimize resource utilization, and meet service level objectives SLOs and service level agreements SLAs. By embracing automation, collaboration, and monitoring, organizations can streamline workflows, enhance productivity, and deliver high-quality software at scale. As technology continues to evolve, DevOps will remain a cornerstone of modern software delivery practices, enabling organizations to stay competitive in today’s fast-paced digital economy.
...Supercharge Your TikTok Content – TikTok Hashtag Generator Tips
In the fast-paced world of social media, TikTok has emerged as a powerhouse platform, capturing the attention of millions of users worldwide. Its unique format of short, engaging videos has made it a go-to platform for content creators and marketers alike. However, with over a billion users, standing out on TikTok can be a daunting task. This is where hashtags come into play, and using a TikTok hashtag generator can be a game-changer for your content strategy. TikTok hashtags are essential for content discoverability and engagement. They categorize your content, making it easier for users to find your videos through searches and trending topics. A TikTok hashtag generator simplifies this process by providing you with relevant and trending hashtags, ensuring your content reaches the right audience. Here are some tips to supercharge your TikTok content using a hashtag generator:
Targeted Hashtags for Niche Content
If your content revolves around a specific niche or topic, it is crucial to use hashtags that cater to your target audience. A TikTok hashtag generator can suggest the best tiktok hashtags that will help you connect with users who share your interests. For example, if you are into cooking, you can use hashtags like #FoodieFinds or #CookingHacks to reach food enthusiasts.
Trending Hashtags for Viral Potential
Trending hashtags can give your content an immediate boost in visibility. TikTok users often explore trending topics, so incorporating these hashtags into your videos can increase your chances of going viral. A TikTok hashtag generator will provide you with the latest trending hashtags, ensuring your content stays relevant and current.
Mix Popular and Less Competitive Hashtags
A balanced approach is key to hashtag success. While using popular hashtags with millions of views can get your content more exposure, it can also drown your video in a sea of competition. Combining popular hashtags with less competitive ones can strike a balance. A TikTok hashtag generator can help you find the right mix to maximize your video’s reach.
Experiment with Hashtag Challenges
TikTok is known for its viral challenges, and participating in them can boost your content’s visibility. A TikTok hashtag generator can help you discover ongoing challenges relevant to your niche. By joining these challenges and using the associated hashtags, you can tap into a larger audience and increase engagement.
Analyze and Adapt
The TikTok algorithm constantly evolves, and what works today may not work tomorrow. To stay ahead, it is essential to analyze the performance of your hashtags regularly. Use TikTok’s built-in analytics tools to see which hashtags are driving the most engagement and adjust your strategy accordingly. A TikTok hashtag generator can help you discover new trending tags to keep your content fresh and engaging.
Create Branded Hashtags
If you are a business or a personal brand, consider creating your unique, branded hashtags. These hashtags can help you build a community around your content and make it easier for your followers to find related videos. A TikTok hashtag generator can assist in brainstorming ideas for your custom hashtags that align with your brand’s message and identity.
...When to Know You Need Mfc140u.dll Uses
Knowing when you need to utilize Mfc140u.dll can be crucial for developers working with Microsoft Foundation Classes MFC and Visual C++ applications. Here are some key indicators that suggest the need for Mfc140u.dll:
- Building MFC Applications: If you are developing Windows applications using the MFC framework and Visual C++, you will almost certainly need to use Mfc140u.dll. Mfc140u.dll is a core MFCDLL ponent of the MFC library and provides the necessary runtime support for MFC-based applications. It contains essential functions, classes, and resources required for the correct execution of MFC code.
- Dependency Check: When you build your application, perform a dependency check to identify whether your project relies on Mfc140u.dll. This can be done using tools such as Dependency Walker or through the build configuration in your development environment. If Mfc140u.dll is listed as a dependency, it means your application is utilizing MFC and requires the presence of this DLL for proper functioning.

- Targeting Windows Platforms: Mfc140u.dll is specifically designed for Windows operating systems, including Windows 7, Windows 8, Windows 8.1, and Windows 10. If your application targets any of these Windows platforms, and you are using MFC, you will need to include Mfc140u.dll as a runtime MFCDLL ponent.
- Multilingual Support: If your application needs to support multiple languages or character sets, Mfc140u.dll is MFCDLL as essential. The u in Mfc140u.dll stands for Unicode, which enables the handling of a broad range of characters and languages. If your application requires multilingual capabilities, Mfc140u.dll ensures proper Unicode support within the MFC framework.
- Redistributable Package: When you distribute your MFC application to end-users, it is important to include the Visual C++ Redistributable for Visual Studio. This redistributable package installs the required runtime vcruntime140.dll ponents, including Mfc140u.dll, on target systems. By including the redistributable package in your application installation, you ensure that Mfc140u.dll is present and accessible on user machines.
- Debugging and Development: During the development and debugging process, you might encounter issues related to MFC functionality. In such cases, it is essential to have the debug version of Mfc140u.dll, known as Mfc140ud.dll, available. The debug version includes additional debugging information and can help identify and resolve issues during development.
- MFCDLL patibility and Updates: Staying up to date with the latest releases and updates from Microsoft is important to ensure MFCDLL patibility and stability. Microsoft regularly provides updates and security patches for Visual C++ and the associated redistributable packages. Monitoring these updates will help you stay informed about changes to Mfc140u.dll and ensure that you are using the most recent and MFCDLL partible version.
In conclusion, knowing when you need to utilize Mfc140u.dll is essential for developers working with MFC and Visual C++ applications. Understanding the role of Mfc140u.dll, performing dependency checks, targeting Windows platforms, requiring multilingual support, including the redistributable package, and staying updated with Microsoft’s releases will ensure the correct usage and functionality of Mfc140u.dll in your applications.
...What You Ought to Consider in Internet Security Blogs?
Internet security has forever been at top worry for IT industry. Since, these days an enormous number of financial exchanges are occurring utilizing the internet based component. PC clients lean toward utilizing web based financial assistance as opposed to sitting tight in lengthy lines for their turn. Some appreciate shopping from their home, and others like to put resources into offer’s utilizing the internet exchanging choice. Every one of this help requires significant certifications of clients, which are known exclusively to the client. The web-based exchange is conveyed forward after the server verifies the entered certifications with the put away qualifications in the server. At the point when the validation cycle is effective, the client then, at that point, can begin the exchange interaction. In this way, at whatever point your PC is associated with internet, there emerges the gamble of infection contamination, wholesale fraud, etc. Here comes the idea of internet security. The difficulties to internet security are to keep the data of the PC client’s no problem at all. Since the digital hoodlums are consistently looking for taking the significant client accreditations.

Essentially, internet security is worried about the insurance of internet records and documents of PC clients from obscure and unapproved client. It is worried about three significant issues like secrecy, accessibility and trustworthiness in pixelroo.com. In internet security, privacy manages keeping up with the data of a client secure and out of reach by unapproved clients. The trustworthy idea manages keeping up with the data of the client unblemished. Furthermore, accessibility is worried about making the data accessible to the client. There are different boundaries utilized for keeping up with the internet security like the utilization of an enemy of infection programming, any best security programming, and a firewall. There are different internet security virtual products accessible on the lookout, which gives total confirmation to the PC clients for offering total protection and security on internet.
The antivirus organizations are offering their programming projects for the preliminary reason for their clients to conclude which one is the best internet security suite to purchase. Grisoft offers free AVG security programming for the preliminary reason. McAfee has likewise presented a preliminary variant for a restricted time of its most recent programming free of charge. These virtual products will keep your PC protected and safeguarded from different inquisitive eyes over the internet. At last, the most ideal choice to dispose of the internet dangers is to disengage from internet. In any case, the utilization of internet has turned into a requirement for the ongoing innovation. Almost, everything is taken care of with internet. This is certainly not a possible choice. The other option is to utilize authorized security programming.
...The most effective method to Pick a Google ads Individual for Your Business
Like anything, it very well may be intense telling the master from the simpleton, yet knowing the right inquiries to pose can ensure that you get the perfect individual Clearly there’s a great deal of other stuff other than these inquiries as these simply covers the nuts and bolts, yet conversing with somebody who is splendid at Bing ads, he continues to go over Google promotion accounts that have been set up by supposed specialists and are only a stunning, one client had 2 distinct individuals work for him, that £5000 was spent on in a solitary month… he had 5 negative watchwords set up (ought to have been 100 as a beginning), he accepted £3000 of that spend was totally squandered.

- Which match types will be utilized on the record?
Brand match will be some unacceptable thing to have as Google concludes what search terms to utilize and that can be extremely expansive – for instance, Google feels that property funds are like compensation day credits. You ought to search for bid state or accurate expression match, for example, on the off chance that you sold window screens ‘window shades’ or “Lumber screens”
- What number of negative catchphrases will you use in the mission?
On the off chance that a word or expression isn’t needed in a pursuit you want to have this in your negative watchword search. Go for the 谷歌广告动态搜索广告 beginning with, and center around things like ‘free’, ‘positions’, and ‘occupation’ including the incorrect spelling of these (single words and broad match)
- What geographic regions are being focused on?
Consider geo-focusing in more modest regions to begin with. Google’s ‘suggested’ boxes are typically centered on Google bringing in cash, so ensure you unstick the ones that aren’t required. You can likewise zero in on geo-changing for explicit regions, for example, ‘Telford’ in the hunt.
- What season of day would you say you are running the adverts and what days?
Season of day and different subtleties rely upon the call of activity on the website page they’re arriving on
- How frequently do you check the pursuit term report?
Accessible from the third day, the reports will provide you with a great deal of the negative catchphrases to add to your negative watchword terms. Ensure that your Bing ads master is wanting to calculate what individuals have looked for to see your advert
- What quality score are the adverts?
5 are the typical beginning score and when individuals navigate, assuming they leave straight away this diminishes your pertinence score. Similarly, when individuals glance around and navigate your pertinence score goes up. Why’s this benefit? The higher the score, the less expensive the navigate, so say the navigate for a score of 5 is £1 each, a score of 10 may be 50p and a score of 1 may be £5 each
...